What is a Log File? Types Explained with Examples

Last updated
If you’ve ever spent hours trying to figure out what went wrong in your code, you know how frustrating it can be without a clear trail to follow. Logs give you that trail, showing the steps your system took before something broke.
Think of stack traces, they’re helpful for showing you where an error occurred. But they don’t always explain how it occurred. That’s where logs come into place.
In this blog, we’ll break down what log files are, why they matter, and how they make debugging and system management easier. Before we take a deep dive, let's understand what exactly is a .log file.
What is a .log File?
A log file is a computer-generated file that records the events, activities, and usage patterns of an application, server, or IT system. These files are essential for monitoring, troubleshooting, and maintaining the performance and security of systems.
For example, imagine a web application with its log file containing every server request or error it encounters. These logs will help developers figure out what’s working, what’s broken, and even how users are interacting with the system. It’s like having a detailed record of the “who, what, and when” of a system’s activity.
Key Uses of Log Files
- Troubleshooting and Debugging
Developers rely on log files to identify and resolve software or hardware issues by analyzing recorded errors and system behavior. - Identifying Issues
Analysts use log data to pinpoint slow queries, detect bugs, and uncover errors that could impact system performance. - Monitoring Network Health
Log files provide critical data for assessing the health of networks and maintaining overall observability. - Enhancing Security
In cybersecurity, log files play a crucial role in detecting unauthorized access, tracking potential threats, and ensuring system integrity. - Ensuring Compliance
IT teams use log files to meet regulatory requirements by documenting system activities and maintaining transparent operations.
What Information Is Typically Found in Log Files?
Log files can include a wide variety of details, such as:
- Timestamps: Indicating when events occurred.
- User Information: Details about user activities.
- Event Information: Logs of specific actions or occurrences within the system.
- Running Applications: Insights into which applications were active.
- Services: Information on system services in use.
- System Errors: Records of errors and malfunctions.
- Kernel Messages: Communications directly from the operating system's core.
How to Open and Edit .log Files
Since log files are typically plain text files, they can be opened with basic text editors or more advanced tools depending on individual purposes.
Using Text Editors
For Windows, you can open with Notepad by right-clicking the file > "Open With" > "Notepad." For macOS, you can open with TextEdit. And for Linux systems, you can open with text editors like Vim, Nano, or Gedit.
Using Code Editors
Tools like Visual Studio Code, Sublime Text, or Notepad++ offer syntax highlighting and better readability.
Using Log Viewers
If you're looking for something specific for logs, tools like LogExpert (Windows) or the tail command (Linux/macOS) allow real-time monitoring of log files.
Using Command Line
On Linux/macOS systems, use cat, less, or tail -f commands to view .log files in the terminal. And for Windows, you can use PowerShell’s Get-Content command.
While it’s not always advisable to edit .log files (to maintain integrity), you can do so for specific cases like removing sensitive information or formatting. Once can use any text or code editor mentioned above to edit the file and save it with the .log extension.
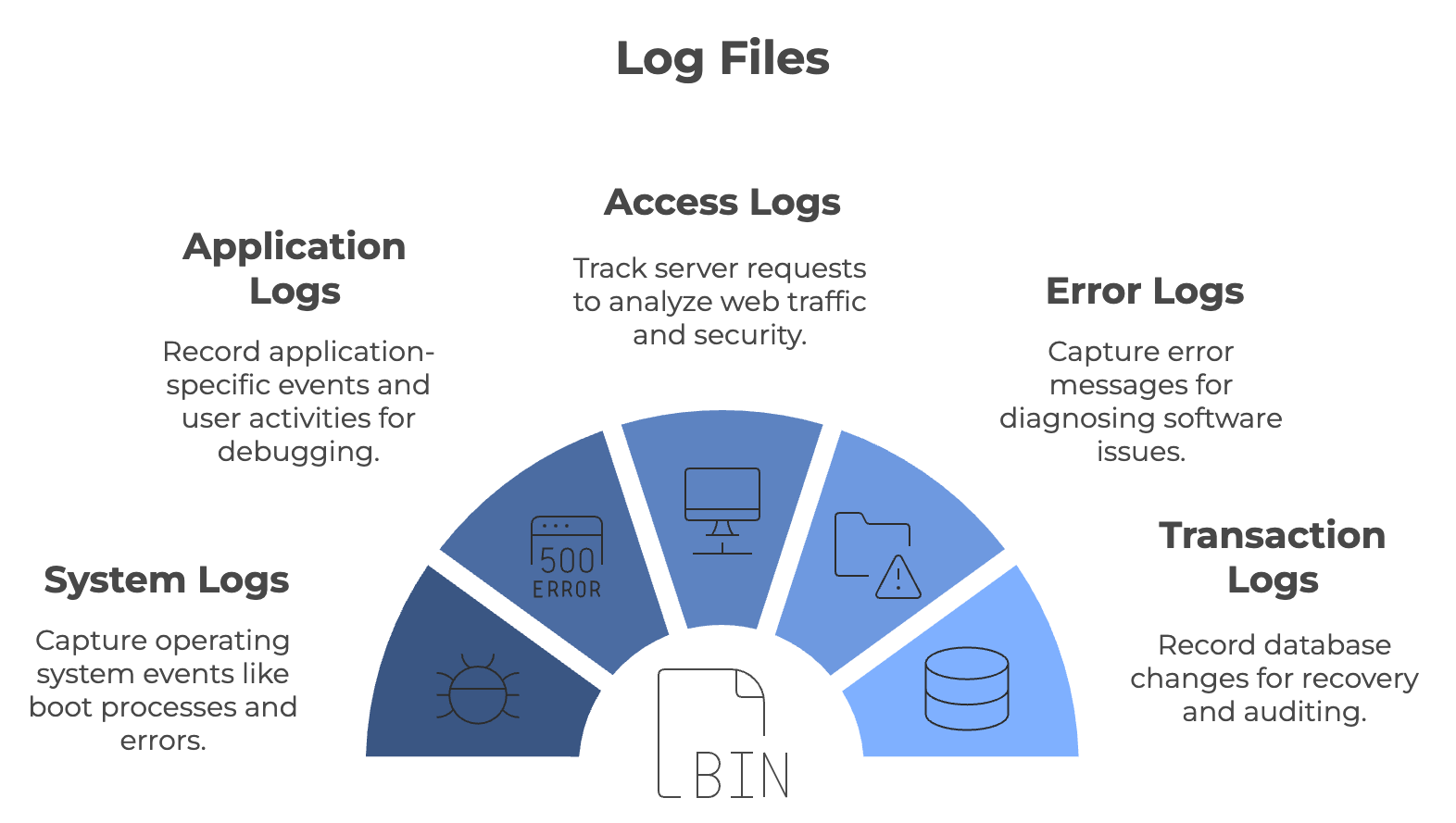
Types of Log Files with Examples
Before we dive in, you have to understand how to read log files. You can either use any text editor or a code editor like Visual Studio. There are several types of log files, each serving a different purpose. Here’s an overview of common log file types with examples:
1. Application Logs
Application logs help track events and activities within a specific application. Developers use application logs to monitor and troubleshoot issues within their software. These logs capture errors, exceptions, warnings, and informational events.
Example:
2024-11-19 08:15:12 - User logged in: user1
2024-11-19 08:16:45 - File uploaded: report.pdf
2024-11-19 08:17:33 - Error: Invalid file format (user1)
2024-11-19 08:18:01 - Successful file processing for: report.pApplication log example
2. System Logs
syslog or System Logs record system-level events, such as operating system operations, device errors, and hardware issues. sysadmin or System administrators use system logs to monitor the health and security of the operating system and hardware.
Example:
Nov 19 08:10:15 myhost kernel: [12345.678901] usb 1-1: new high-speed USB device number 3 using xhci_hcd
Nov 19 08:11:00 myhost systemd[1]: Started Apache HTTP Server.
Nov 19 08:15:22 myhost kernel: [12547.123456] eth0: link down
Nov 19 08:16:10 myhost systemd[1]: Stopping MySQL Database Server...Sys log example
3. Security Logs
These logs capture security-related events, including login attempts, unauthorized access, and changes to security settings. Security analysts rely on these logs to detect and respond to potential security incidents.
Example:
2024-11-19 08:00:15 - Failed login attempt: user1, IP: 192.168.1.10
2024-11-19 08:05:47 - Successful login: user2, IP: 192.168.1.12
2024-11-19 08:10:30 - Unauthorized access attempt: user1, IP: 192.168.1.20
2024-11-19 08:15:02 - User1 password changed.Security log example
4. Access Logs
As the name defines, access logs track access to resources, applications, or systems, detailing who accessed what and when. IT and security teams use access logs to monitor user activity and verify that access control policies are being followed.
Example:
2024-11-19 08:00:01 - User user1 accessed /dashboard
2024-11-19 08:05:12 - User user2 accessed /reports
2024-11-19 08:06:05 - User user3 attempted to access /admin (Denied)
2024-11-19 08:10:00 - User user1 logged outAccess log example
5. Audit Logs
These logs provide a chronological record of system and application activities, especially changes made by users or administrators. Auditors and compliance officers use audit logs to ensure that systems comply with regulatory and security standards.
Example:
2024-11-19 08:00:01 - User user1 created a new report.
2024-11-19 08:05:00 - User user2 modified report: report.pdf
2024-11-19 08:10:30 - Admin user3 deleted report: old_report.pdf
2024-11-19 08:15:00 - User user1 granted access to report.pdfAudit log example
6. Error Logs
Error logs capture information on application or system errors, warnings, and exceptions. Developers and IT teams use error logs to diagnose and resolve issues within systems and applications.
Example:
2024-11-19 08:00:15 - Error: Database connection failed (Timeout)
2024-11-19 08:05:22 - Warning: Disk usage exceeded 90% on /dev/sda
2024-11-19 08:10:00 - Error: File not found: report.pdf
2024-11-19 08:12:55 - Error: Null pointer exception in function handleRequest()Error log example
7. Transaction Logs
Record all transactions performed by an application or database, providing a history of changes and actions. These logs are used in database management and financial applications to ensure data integrity and provide rollback capabilities.
Example:
2024-11-19 08:00:15 - Transaction started: Sale of item123, amount: $100
2024-11-19 08:05:22 - Transaction completed: Sale of item123, amount: $100
2024-11-19 08:10:00 - Transaction failed: Refund of item123, reason: Insufficient funds
2024-11-19 08:15:05 - Transaction reversed: Refund of item123, amount: $100Transactional log example
8. Event Logs
Event logs record specific events or activities within a system, including scheduled tasks, system updates, and maintenance events. IT teams and system administrators use event logs to track system and application events for troubleshooting.
Example:
2024-11-19 08:00:01 - System update started: Patch KB1234567
2024-11-19 08:10:00 - Scheduled task executed: Backup completed
2024-11-19 08:15:23 - System update completed: Patch KB1234567 applied8. Debug Logs
Debug logs capture detailed information on program execution, often used in development and testing environments. Developers use debug logs to gain insights into the code execution and find bugs.
Example:
2024-11-19 08:00:01 - Debug: Entered function processRequest()
2024-11-19 08:05:15 - Debug: Variable "userData" initialized with value: {"name": "user1", "age": 30}
2024-11-19 08:10:05 - Debug: API response received: {"status": "OK", "data": {"report": "report.pdf"}}
2024-11-19 08:12:00 - Debug: Exited function processRequest()10. Network Logs
Network logs capture data related to network traffic, bandwidth usage, and connections. Network administrators use network logs to monitor traffic, detect unusual activity, and optimize network performance.
Example:
2024-11-19 08:00:01 - Connection from IP 192.168.1.10 established on port 80
2024-11-19 08:05:12 - Bandwidth usage: 100MB, Device: Router1
2024-11-19 08:10:20 - Suspicious activity detected from IP 192.168.1.15, possible DDoS attack
2024-11-19 08:15:00 - Connection from IP 192.168.1.10 closedImportance of Monitoring Log Files
Log files play a critical role in ensuring the reliability, security, and performance of systems and applications. Here’s why monitoring them is crucial:
1. Troubleshooting and Debugging
Log files help identify the root cause of application crashes, errors, or unexpected behavior. They provide detailed insights into what went wrong and when.
2. Performance Optimization
By analyzing log data, administrators can spot inefficiencies, bottlenecks, or high resource consumption, enabling proactive system optimization.
3. Security
Monitoring linux logs for unauthorized access attempts, malware activities, or unusual behavior helps detect potential security breaches.
4. Compliance
Many industries require maintaining and monitoring logs to comply with regulatory standards like GDPR, HIPAA, or PCI-DSS.
5. Audit Trails
Logs provide a chronological record of activities, ensuring accountability and transparency in systems and applications.
6. Proactive Monitoring
Real-time log monitoring allows detecting and resolving issues before they impact users. Alerts can be configured for anomalies or thresholds.
7. Incident Management
In Site Reliability Engineering (SRE), logs play a vital role in managing incidents, analyzing patterns, and minimizing downtime.
Best Practices for Log Monitoring
Monitoring log files is a critical practice for maintaining system reliability, security, and performance. Here’s how to ensure effective log monitoring:
- Use centralized logging tools like ELK Stack (Elasticsearch, Logstash, Kibana), Splunk, or Datadog.
- Configure alerts for critical events.
- Retain linux logs based on your organization’s policies and compliance requirements.
- Regularly review and analyze logs for trends or anomalies.
Monitoring .log files ensures a well-maintained, secure, and reliable system while enabling quick responses to potential issues. While this is just an overview, we have a detailed blog that discusses the best practices for log monitoring here.
Logs are often not considered as important but formatting them and keeping them organized goes a long way. We hope this guide was helpful for you to understand everything you need to know about log files and its types.
Frequently Asked Questions (FAQs) on Log File
What is in a log file?
A log file contains detailed records of events, transactions, or activities that occur within a system, application, or device. These entries typically include timestamps, event types, error codes, user actions, and system statuses, helping to track and troubleshoot system behavior.
How do I open a log file?
You can open a log file using text editors, command line tools and log management tools lile ELK stack or DataDog.
Where are the log files?
Log files are typically stored in specific directories, depending on the system or application:
- Linux/Unix: Commonly in /var/log/.
- Windows: Usually in C:\Windows\System32\LogFiles\ or within application folders.
- Applications: Many apps store logs in their own directories, often under a folder named logs or similar.
What is a log file used for?
Log files are essential for debugging, monitoring, security, auditing, and analysis. Here's a detailed breakdown:
- Debugging: Identifying and resolving software issues.
- Monitoring: Tracking system performance and behavior.
- Security: Detecting unauthorized access or anomalies.
- Auditing: Recording user actions for compliance and accountability.
- Analysis: Identifying trends or patterns in system activity.
What is the format of a log file?
Log files are typically stored in plain text formats, such as TXT, JSON, CSV, XML, or specialized binary formats as per the system. Here's a detailed breakdown:
- TXT: Simple text files.
- JSON: Structured logs for better parsing.
- CSV: Logs stored in a tabular format for easy import into spreadsheets.
- XML: Hierarchical, machine-readable logs.
What is the difference between a log file and data file?
Log File contains records of events and system activities, designed for monitoring, debugging, and analysis. While a data file stores application-specific data, such as databases, user inputs, or configuration settings, used directly by the application to function.
Rohan Taneja
Writing words that make tech less confusing.



